The Inter has dramatically transformed global communication making it easy for people around the world to exchange information. But, it simultaneously poses a very serious problem. Everyone can access the Internet, but not everyone has good intentions. Some people misuse the computer software programs, while others hack we understand the potential risks that our computer and its data are exposed to and take adequate precautions to protect it from hazards.
Computer Viruses:
You are all familiar with the word virus that is generally mentioned in connection with your health. Whenever you catch a common cold or have fever, the first thing that your parents and the doctor seem to suspect is that you might have caught a virus. The term virus generally gives us an impression of a biological infection that affects out body. A computer to computer, usually via shared software and damage other programs stored on the computer. The ‘virus’ program is often attached by the human perpetrator to a genuine program and is not readily detectable. And viruses affect our computers and our computers affect many computers.
In the recent years, the term virus has been increasingly mentioned in connection with the computers and must have heard about it too. Let us try to understand what a Computer Virus is and how it affects us our computer system.
Computer Viruses attack computer systems just as biological viruses attack the humans. They infect generally the hard disk file and corrupt the operating system. They spread to other computers that exchange some information (files) with the infected computer. In simple words, a computer virus is a program written with a malaise intention which can execute and replicate itself on your computer without your knowledge and consent.
In this lesson, you will learn about viruses and how they work and also understand how to protect your computer and its data.
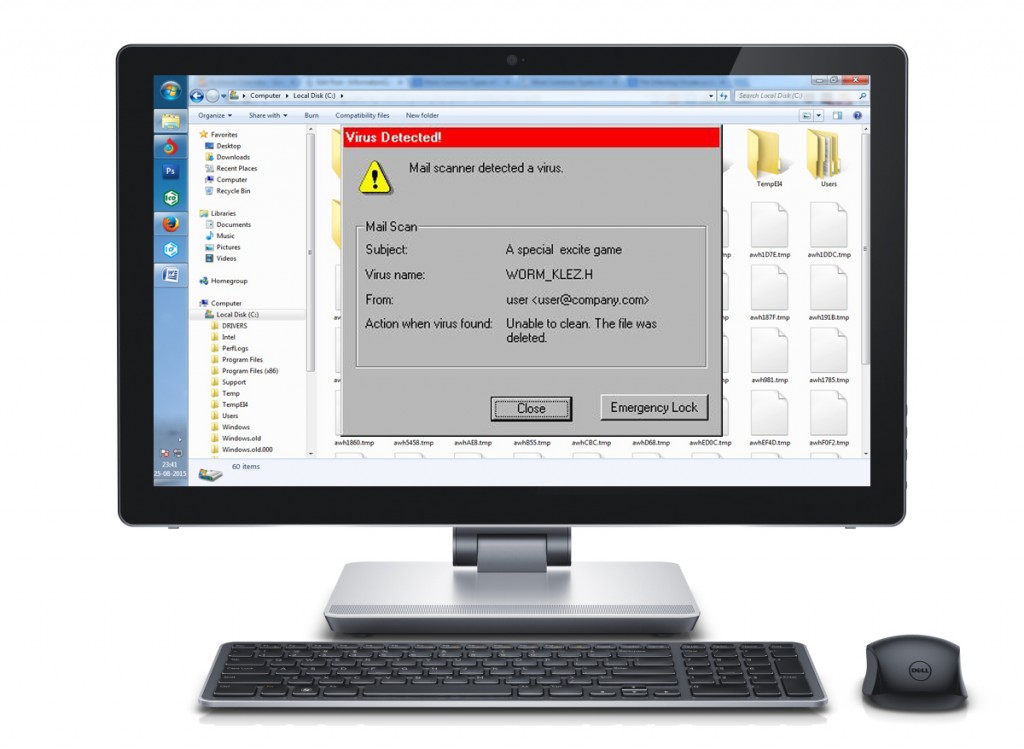
There are over forty thousand known viruses and more are being introduced every day. Some viruses are relatively harmless. They just attach to the outgoing messages or the emails and these attach to your Address book. Then they spring to life to do their dirty deeds. Sometimes, a strange message appears on your screen, which may be virus in modified form. In the worst case, all the contents of your hard drive may be virus in modified from. In the worst case, all the contents of your hard drive may be wiped out.
In 1988, a student at Cornell University sent out a virus by accident, Infecting more than 6,000 computers within minutes, nearly bring the that it forced Microsoft and a number of other very large companies to completely to completely turn off their e-mail systems until the virus could be contained.
In January 2004, the doom worm infected approximately a quarter-million computers in a single day.
Types of Infection:
There are three types of programs that can infect a computer.
- Viruses
- Worms
- Trojan horses
Viruses, Worms and Trojan Horses are human-made programs created specifically to wreak havoc on personal computer and networks.
Viruses:
A virus is small piece of software that piggybacks on real programs. For example, a virus might attach itself to a program such as a spreadsheet programs. Each time the spreadsheet program runs, the virus runs too, and it has the chance to reproduce itself (by attaching to other programs). In more technical language, it is an executable cods which attaches itself to, overwrites or replaces another program in order to reproduce itself on your computer without your knowledge and consent. The virus spreads when you launch programs from an infected disk or download files from the Internet.
The following viruses affect our computer:
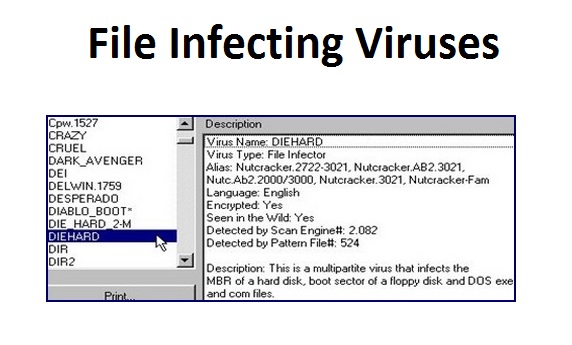
File Infecting Viruses:
These types of viruses infect the files.
When an infected file is executed the virus code gets loaded into the primary memory and keeps running in the background as long as the computer remains on. This gives the virus a very effective way to replicate itself. When another file is executed, the virus code gets attached to this file and writes the modified file into the disk.
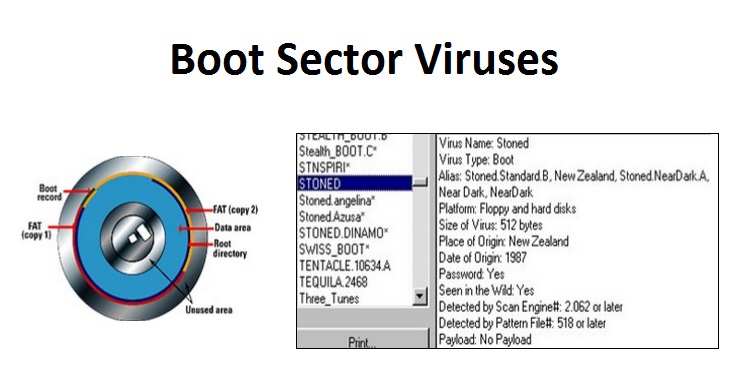
Boot Sector Viruses:
This type of viruses generally infects the hard disk and floppy disk. The boot sector is the very first sector of a disk that contains a small program that is the first part of the operating system that the computer loads. It is a tiny program that tells the computer how to load the rest of an operating system, exe.com or sys.ect. By putting its code in the boot sector, a virus can guarantee its execution. It can load itself into the primary memory immediately, and is able to run as long as the computer remains on. Boot sector viruses spreads can infect the boot sector of any floppy disk inserted in the machine. Such viruses spread like a wildfire on school and college campuses where many persons share the same machines.
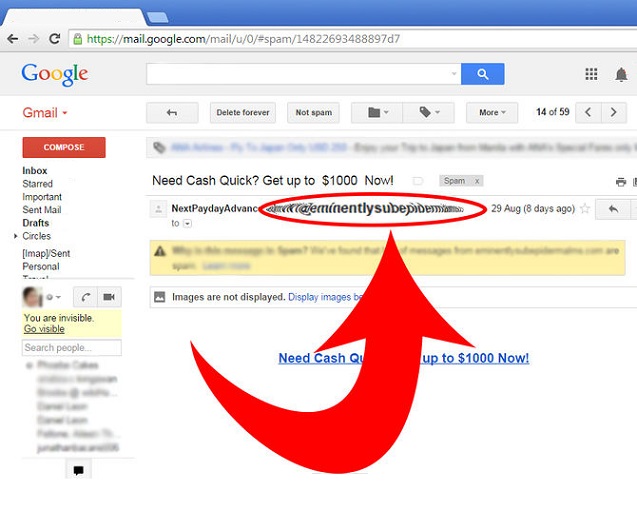
E-mail Viruses:
E-mail Virus is the latest thing in the world of computer viruses. An E-mail virus moves around in e-mail messages, and generally replicates itself by automatically mailing itself to dozens of people in the victim’s E-mail Address book.
In March 1999, a virus called Melissa spread in Microsoft Word documents sent via E-mail. Someone created the virus as a Word document and uploaded it to an Internet Newsgroup. Anyone who downloaded the document (and therefore itself) in an e-mail message to the first 50 people in the person’s Address book. The Melissa virus spread very fast. In fact it was the fastest-spreading virus. It forced many large companies to completely shut down their e-mail systems.
Worm:
It is a small piece of software that can copy or replicate itself. It doesn’t need to attach itself to any other program to replicate. It spreads though computer networks and security holes. A copy of the worm scans the network for another machine on the network that has a specific hole. To copy itself to the new machine it uses the security hole, and then starts replicating from there, as well.
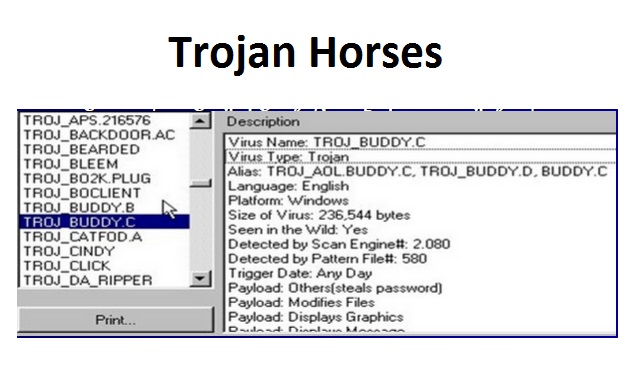
Trojan Horses:
Named after the famous horse of troy, a Trojan horse is simply a computer program that claims to do one thing but instead does something else when you run it. Trojan house is a type of virus that pretends to be a useful program, such as a game or a utility program, when in reality it contains special code that will intentionally damage any system into which it is loaded.
Trojan horses have no way to replicate themselves automatically.


Leave a Reply